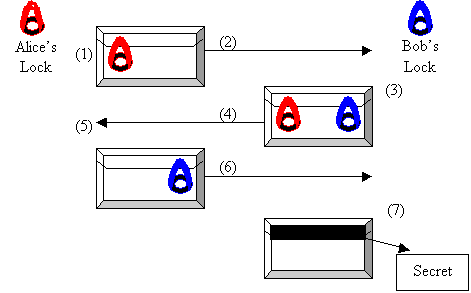
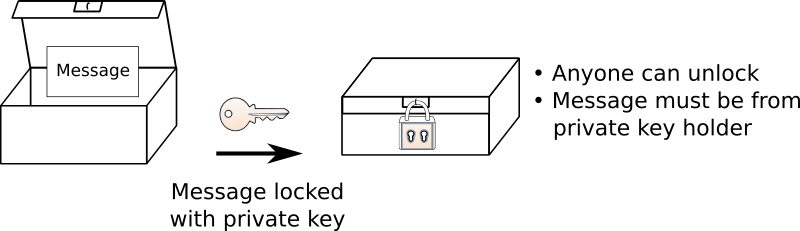
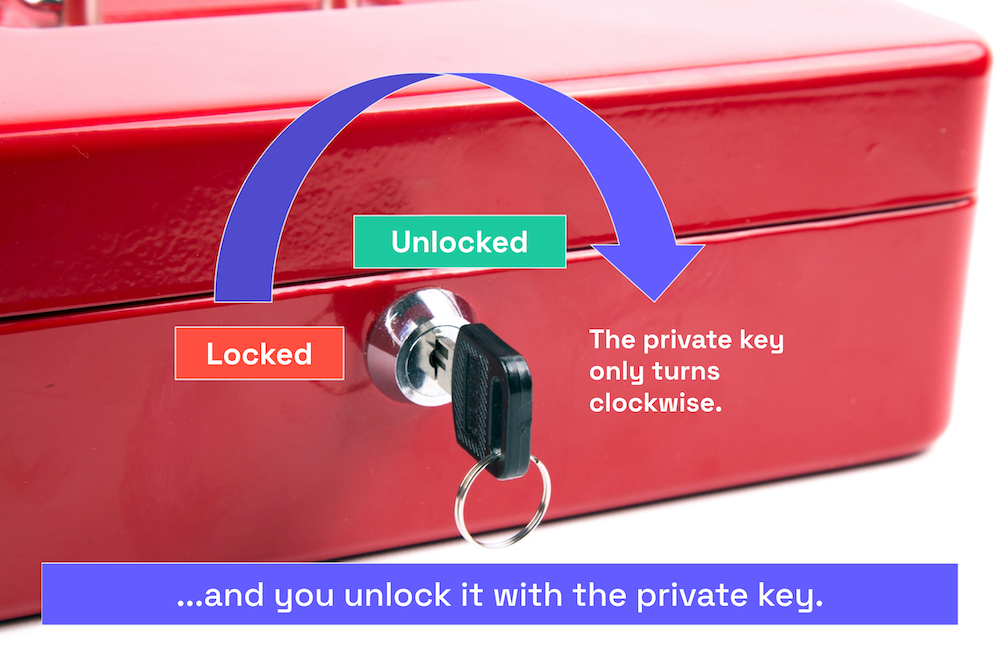
Lock Protect Guard Key Security Private Comments - Key Lock Icon Png Transparent PNG - 980x958 - Free Download on NicePNG

Premium Vector | Concept of private key in cyber security technology, graphic of lock pad combine with binary code and electronic key